Introduction
In the world of web3, markets, narratives, and memes have been broken and built around the question of digital asset ownership. As an output of this dichotomy, the crypto world has produced two types of wallet primitives: custodial and non-custodial wallets. A non-custodial wallet (also known as self-hosted), grants users full control over their private keys and, consequently, their cryptocurrency holdings. Unlike custodial wallets, where a third party holds and manages the keys, self-hosted wallets ensure that only the owner has access to their funds.
By now, it is not a secret that the blockchain industry likes to create a rabbit hole around every technology/product type, and there is no reason why wallets should be an exemption. To this end, the market has given birth to multiple subtypes of self-hosted wallets including hardware wallets, hot, cold, desktop, mobile, and web wallets – each offering unique feature sets and security levels. However, what unites every self-hosted wallet, is the fundamental principle encapsulated in the phrase: “Not your key, not your crypto,” emphasising that the true ownership and security of digital assets lie in holding one’s private keys.
In this guide, we aim to introduce you to each type of non-custodial wallet, so that, hopefully by the end, you can decide for yourself which one to choose as your companion in this multifaceted, yet fascinating world of crypto…
Hardware Wallets
Hardware wallets are physical devices designed to store the private keys necessary for accessing and managing cryptocurrency holdings. Unlike software wallets that store private keys on a device connected to the internet, hardware wallets store these keys offline, significantly enhancing security. They function as secure gadgets that safeguard sensitive information, isolating private keys from potentially compromised computers or smartphones.
Popular hardware wallets in the market include:

Why Go for Hardware Wallets?
Hardware wallets are renowned for their security. By keeping private keys offline, they are immune to online threats such as malware, phishing attacks, and keyloggers. Transactions are signed within the device, ensuring private keys never leave the hardware wallet, even when connected to a computer or mobile device.
Even if your computer was to be infected with malware, the private keys remain secure because your keys are stored on a separate device. To further their security proposition, many hardware wallets like Ledger, incorporate additional security measures such as PIN codes, passphrases, and biometric verification, thus adding multiple layers of protection against unauthorized access.
You might want to consider…
Let’s admit that while hardware wallets are highly secure against digital threats, they are susceptible to physical damage or loss. If a hardware wallet is lost or destroyed without a proper backup of the recovery seed, the stored cryptocurrencies can be permanently inaccessible.
Furthermore, unlike software wallets, which are free to download 9 out of 10 times, hardware wallets come with a cost. The price of these devices can range from around $50 to several hundred dollars, which might be a deterrent for some users, especially those new to cryptocurrency.
Lastly, although hardware wallets provide superior security, they can be less convenient for frequent transactions. The process of connecting the hardware wallet to a laptop, entering PIN codes, and confirming transactions on the device can be cumbersome compared to the instant access provided by software wallets.
So what’s the verdict then?
A simple answer is that security and peace of mind come with costs, both monetary and experience-related. If you are someone who looks to join a degen telegram group and trade memcoins every 10 minutes or so, then a hardware wallet is probably not the best choice for you. But, for those who want to pass down their hard-earned BTC to their grandchildren, then hardware might be your best bet.
Self-hosted Software Wallets
Self-hosted software wallets are non-physical wallets where the custody and management over given crypto assets lie within the owner. Self-hosted software (or “hot”) wallets come in a few different forms including desktop, mobile, web, browser, and full-node wallets. One wallet service provider can offer a mix of the mentioned wallet types under their brand. For example, Metamask provides an app, desktop, and browser wallets. We explain each subtype of Self-hosted wallets below.
Subtype: Self-hosted Desktop Wallets
Desktop wallets are a type of self-hosted software wallet installed directly onto a desktop or laptop computer. These wallets provide users with full control over their private keys and the ability to manage their cryptocurrency holdings independently of third-party services. By running on the user’s own hardware, desktop wallets can offer a blend of accessibility and security, assuming the host computer is maintained properly.
Some of the most prominent desktop wallets include:
- Phantom: Known for its speed and efficiency (takes about 12 seconds to set up), it is a lightweight wallet that offers advanced features such as integration with dApps and in-wallet staking.
- Exodus: A user-friendly wallet that supports a wide range of cryptocurrencies, Exodus combines an intuitive interface with powerful features like bridges and NFTs, making it popular among both beginners and experienced users.
To interact seamlessly with blockchain networks, many self-hosted wallets use RPC (Remote Procedure Call) services. RPC enables wallet software to communicate with blockchain nodes for actions such as querying transaction data, broadcasting transactions, and retrieving account information. For example, MetaMask sends RPC requests to a node to check balances or send tokens. Providers can ensure reliable and secure blockchain interactions and advanced functionalities like in-wallet staking, custom transaction fees, and dApp integration, via Simply’s API services, which provide access to 60+ networks across multiple ecosystems with tier 3 datacenter infrastructure and dedicated tooling & monitoring.
Desktop Wallets Offering:
Desktop wallets provide users with full control over their private keys and transaction management. This autonomy is crucial for those who prioritise independence and do not wish to rely on third-party services.
When run on a clean, malware-free computer, desktop wallets can offer conditional security, assuming that users employ caution such as default usage of VPNs and blockage of public WiFi networks. But generally, desktop wallets are less susceptible to online attacks compared to web wallets, as long as the computer remains secure and properly maintained.
As a cherry on top of your vanilla ice cream, desktop wallets offer advanced features such as custom transaction fees, detailed transaction history, and integration with hardware wallets, making them suitable for power users, traders, and developers.
But before you download…
The security of a desktop wallet heavily depends on the integrity of the host computer. If the computer is infected with malware, keyloggers, or other malicious software, private keys can be compromised, leading to potential loss of funds. Make sure to avoid dodgy emails and not actually click on the buttons that tell you to “click this button for free cruise tickets”.
Also, desktop wallets require frequent updates to ensure they remain secure and compatible with the latest blockchain protocols. You must stay vigilant about applying software updates and security patches because of course, you do not want to be tricked into fake software updates, just like Electrum’s users in 2019.
Who is a desktop wallet made for?
More specifically, this one might be handy for developers who want to connect crypto with their developer environment, for those who already have hardware wallets and might as well continue in the same gadget, or probably for those ones who do some advanced stuff like Liquidity Provision, Flash Loans or DEX arbitrage. But hey, if none of the above descriptions landed, but you want to access crypto via desktop, then do go for it.
Subtype: Self-Hosted Mobile Wallets
Self-hosted mobile wallets are applications installed on smartphones that allow users to manage their cryptocurrency directly from their mobile devices. These wallets often store private keys locally on the phone, providing users with control over their funds while offering the convenience of managing digital assets on the go.
Notable examples of self-hosted mobile wallets include:
- Trust Wallet: A highly popular mobile wallet with 70 million users, known for its ease of use, extensive support for various cryptocurrencies, and integration with decentralised applications (dApps).
- Rabby Wallet: Popular in the eastern community, offering slick user experience (UX) and rare functionalities like gas top-up and integrated DEX.
As seamless as it gets?
It’s a no-brainer that mobile wallets excel in convenience, allowing users to make quick and easy transactions from anywhere, thus making them ideal for daily use, such as paying for goods and services (see CityPay or Xaman Tangem) or transferring funds on the go.
Furthermore, many mobile wallets are designed with user-friendliness in mind. Features like biometric authentication (facial recognition, fingerprint scanning) and simplified login processes (email or social login) make them accessible even to those who are new to cryptocurrency.
With a mobile wallet, users can access their funds anytime and anywhere, as long as they have their smartphone and network connection with them. This accessibility is a significant advantage for users who need to manage their assets on the move.
Easy to use, (but) easy to lose:
The primary risk with mobile wallets is the potential for phone theft. If a phone is stolen, there is a risk that an unauthorised person could access the wallet if it is not adequately secured with strong passwords or biometric authentication. If your pass is 1111 or 2580, please change…
Mobile devices can be targets for malware, including keyloggers and malicious apps designed to steal private keys or sensitive information. You must be cautious about downloading fake apps and don’t make the same mistake that I did when downloading the fake Trezor app and nearly getting my precious memcoins taken away from me (I was a newbie back then).
Everyone has one, you might as well too.
By now it’s probably clear that holding your life savings on an app is not the wisest thing to do. However, mobile wallets can make your crypto life efficient and fun, whether it’s sending your friend some USDT, paying for beer in BTC, or buying DOGE right after Elon tweets about it.
Subtype: Self-Hosted Web Wallets
Self-hosted web wallets are cryptocurrency wallets that can be accessed through a web browser. These wallets most likely store private keys within the browser’s local storage, enabling users to manage their digital assets from any device with internet access.
Some examples of self-hosted web wallets include:
- MetaMask: A browser extension wallet primarily used for interacting with the Ethereum blockchain and dApps. It supports hundreds of tokens and integrates with popular web browsers like Chrome and Firefox.
- Coinbase Wallet: Separate from the Coinbase exchange, Coinbase Wallet is a self-hosted wallet that allows users to store their private keys and access a variety of decentralised applications. It offers a seamless user experience by being connected to the Coinbase exchange, allowing for frictionless on and off-ramping.
Gateway to DeFi – in your browser.
Web wallets can be accessed from any device with an internet connection and a web browser. To this end, browsers are convenient for users who need to manage their assets from different locations or devices.
A definite advantage of web wallets is that they can be set as Chrome, Firefox, or any other search engine extensions, which in turn allows a near-automatic connection with DeFi platforms, NFT marketplaces, and delegation of your coins to a validator like Simply Staking for staking purposes.
Additionally, web wallets provide a middle ground between mobile and desktop wallets. For example, you can have a web wallet both on your Safari app and laptop Safari browser, instead of downloading a desktop app and an AppStore app on each device, or do a mixture that best fits your needs.
Security Considerations:
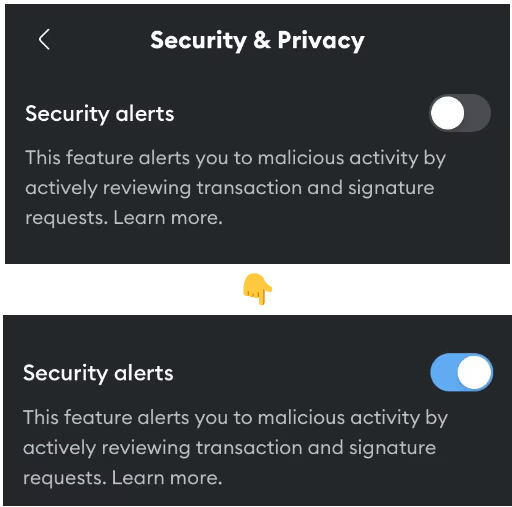
Web wallets are vulnerable to phishing attacks. Malicious actors can create fake websites or browser extensions that mimic legitimate web wallets to steal users’ private keys and funds. So before you choose to fund a web wallet, go to the section called “security” or “security & privacy” and look for buttons like “alerts”, “scanners” or “transaction signing” and turn those on. See how you can do it on Metamask below:
While web wallets provide convenience, they do not offer the same level of security as hardware wallets. Since private keys are stored in the browser’s local storage, they are more exposed to potential threats like browser vulnerabilities and malware. For example, the “Shitcoin Wallet” was a malicious Chrome browser extension claiming to manage Ethereum and ERC-20 tokens. Once installed, it injected malicious JavaScript into cryptocurrency-related web pages, stealing private keys and sensitive data, hence allowing attackers to gain control of users’ wallets and initiate unauthorised transactions to steal funds.
Opinion on web wallets:
Self-hosted web wallets strike a balance between accessibility and functionality, making them a popular choice for managing cryptocurrencies. While they offer significant convenience and ease of use, they come with inherent security risks that require users to be vigilant against phishing and other online threats. Although some mobile wallets provide integrations with dApps, the interaction might not be as user-friendly experience as web wallets. So if you are someone who wants to dive deep into the rabbit hole of crypto or do some comprehensive desktop research and development, a web wallet is your best friend.
Subtype: Full Node Wallets
Full node wallets are a type of cryptocurrency wallet that stores the entire blockchain on the user’s device. By maintaining a complete copy of the blockchain, full node wallets independently verify all transactions and blocks, contributing to the security and decentralisation of the network. These wallets not only manage private keys but also participate in the blockchain’s consensus mechanism by validating transactions.
Leading examples of full-node wallets include:
- Bitcoin Core: The original Bitcoin wallet, Bitcoin Core is a full node client that stores the entire Bitcoin blockchain. It offers high security and complete control over transactions, making it a preferred choice for users who prioritise privacy and decentralisation.
- Geth: Short for Go Ethereum, Geth is the most popular full node client for the Ethereum network. It enables users to store the entire Ethereum blockchain, validate transactions, and deploy smart contracts.
It does not get more decentralised…
Full node wallets provide users with unparalleled control over their transactions. By independently verifying every transaction and block, users can ensure that their transactions are valid without relying on third parties. Such autonomy enhances the integrity and trustworthiness of the blockchain network.
Using a full node wallet improves user privacy, since participants validate transactions themselves, they do not need to share transaction data with external servers or nodes, hence reducing the exposure of transaction information and helping maintain user pseudonymity.
Additionally, running a full node contributes to the overall health and decentralisation of the blockchain network. Full nodes help enforce consensus rules, propagate transactions and blocks, and enhance the network’s security by making it more resistant to attacks.
You will probably need a PC (or two)
Full node wallets require substantial storage space to store the entire blockchain. As the blockchain grows over time, users need to allocate increasing amounts of disk space. For example, the Bitcoin blockchain is over 450+ GB and continues to grow.
Operating a full node involves significant bandwidth usage, as nodes must continuously download and upload data to stay synchronised with the network. This can be a constraint for users with limited internet bandwidth or data caps.
Last but not least, running a full node demands considerable computing resources. Users need a powerful CPU (computer processing ability), sufficient RAM (computer memory), and reliable internet connectivity to ensure smooth operation. Resource intensiveness can thus be a barrier for users with limited hardware capabilities.
Overall thoughts:
Resource intensiveness and the requirement for tech expertise are definite barriers to the full node wallets. Full node wallets can be useful for those who want to set up validator nodes in their garage but are not suitable for daily retail users.
Subtype: Paper Wallets
Paper wallets are a form of cryptocurrency storage that involves printing the private and public keys on a physical medium, typically paper. This method ensures that the keys are kept entirely offline, providing a high level of security against online threats. Paper wallets are generated using tools or websites, such as BitAddress, which create keys offline to prevent exposure to the internet.
Paper wallets, are pretty much a thing of the past, and used to be generated using websites or tools like:
- BitAddress: An open-source tool for generating Bitcoin paper wallets. It operates offline to maximise security during the key generation process.
- MyEtherWallet (MEW): A popular tool for generating Ethereum paper wallets. Users can download the MEW application and create paper wallets offline.

Old, but (kind of) secure:
Post-generation, paper wallets are not connected to the internet, making them immune to online hacking attempts, malware, and phishing attacks. Additionally, during the usage phase, paper wallets do not rely on any digital storage medium that could be compromised, ensuring the private keys are kept safe from cyber threats. The fact that these wallets resemble more traditional forms of money such as bank notes, could make them appealing to less tech-savvy users.
Be careful in the rain!
Despite their simplicity, paper wallets are susceptible to physical damage and loss. They can be destroyed by fire, water, or simply misplaced. Once lost or damaged, the private keys are irrecoverable (assuming there is no alternative storage set up), resulting in permanent loss of the associated funds.
Moreover, conducting transactions with a paper wallet is nowhere near as simple as with a mobile or desktop wallet. Users need to manually enter the private key or scan a QR code to transfer funds, making it impractical for frequent transactions. Additionally, reusing the private key for multiple transactions can compromise its security.
A security vulnerability can be exposed if we take a step back. During teh generation phase, users can be misguided by scam paper wallet generator websites, that can drain their wallets anytime. Before accessing a paper wallet website, make sure to check it with link scanners such as NordVPN’s link checker and avoid websites similar to the one below:
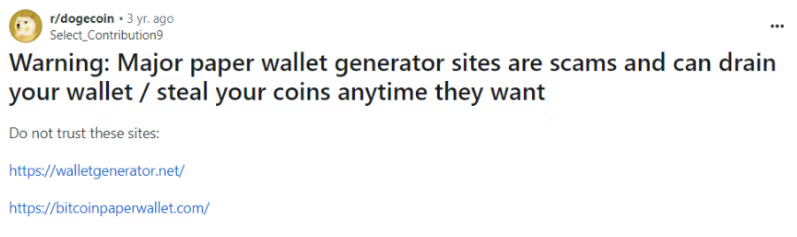
Final assessment:
The security of a paper wallet depends heavily on how it is generated. Using an insecure or compromised computer to create a paper wallet can expose the private keys to potential theft. Paper wallets are probably useful hooks to get your grandpa or uncle Bob into crypto, but in the midst of the tech-dominated and innovation-driven world of crypto, it is hard to find a compelling reason why someone would still use them.
Subtype: Brain Wallets
Brain wallets are a type of cryptocurrency wallet where the private key is generated from a passphrase that the user memorises. Memorisation method relies on the user’s ability to recall their passphrase, which is then used to create the corresponding private key. Hence, the main appeal of brain wallets is their lack of any physical or digital footprint, as the security relies solely on the user’s memory.
Portable, hidden, and cheap:
Since the private key is generated from a passphrase and not stored anywhere physically or digitally, brain wallets eliminate the risk of physical theft, hardware failure, or digital hacking. This makes them particularly appealing to users who prefer not to rely on hardware or paper storage methods.
Brain wallets are as portable as the users themselves. As long as the user can remember the passphrase, they can access their cryptocurrency from any location and any device with the necessary tools to regenerate the private key.
Unlike hardware wallets or other secure storage methods, brain wallets do not require any physical materials or devices, making them a cost-effective solution for storing cryptocurrencies.
Let’s create a brain wallet together!
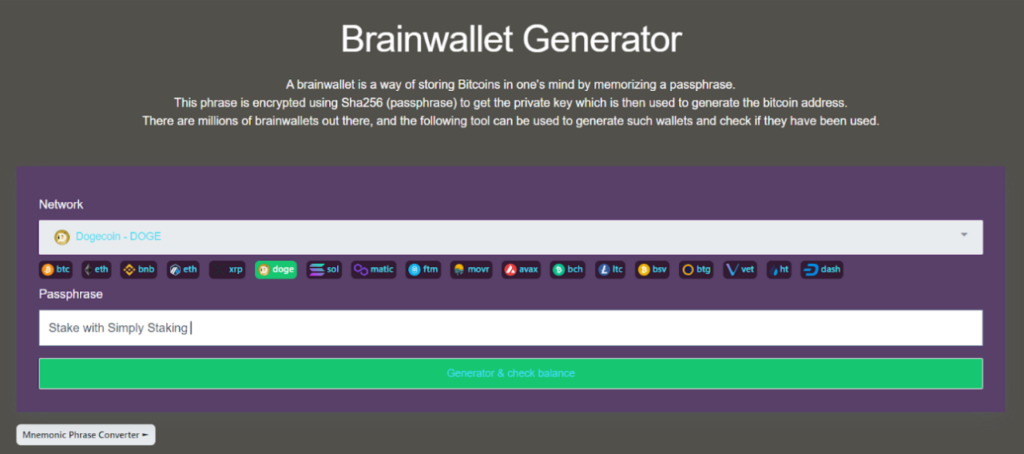
Step 1: access a brain wallet creator such as the PrivateKeyFinder.io
Step 2: Choose which network you want to create your wallet on and enter your passphrase. As shown, I chose Dogecoin with passphrase of “Stake with Simply Staking”
Step 3: Press “Generate & check balance” to generate your brain wallet.
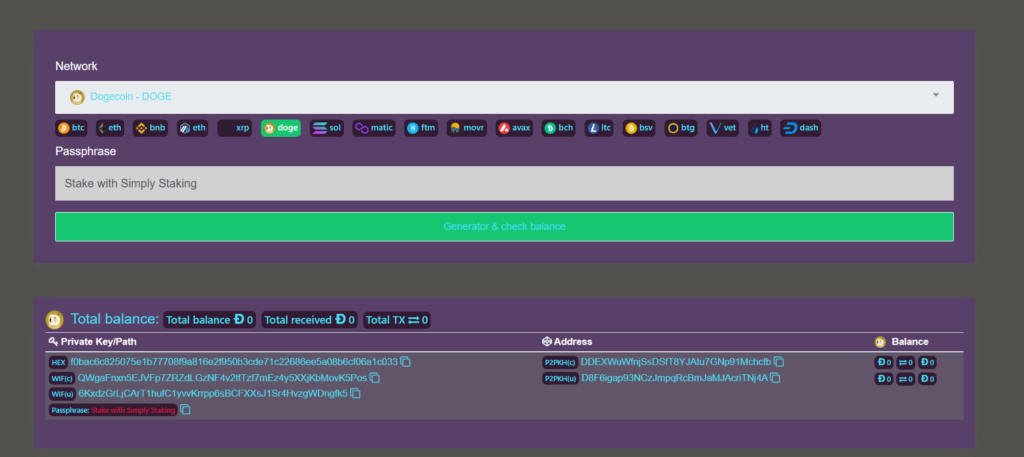
Step 4: Check your “Total balance” and memorise your passphrase displayed at the bottom right corner of the board.
Congrats! You have set up your brain wallet. Wait, not so fast tho…
Your bank is as strong as your memory & as weak as your password:
The security of a brain wallet heavily depends on the strength and complexity of the passphrase. Simple or common phrases are vulnerable to brute-force attacks, where attackers systematically try different combinations to guess the passphrase. Ensuring the passphrase is sufficiently complex and unique is crucial to avoid this risk. The links below represent just a handful of attack tools that a hacker could use:
Additionally, if a criminal discovers the existence of your brain wallet, they could hold you hostage until you release the private key—an option not feasible with an offline wallet. Furthermore, there is always the risk of forgetting your private key, which would result in the permanent loss of access to your funds.
Conclusion:
Brain wallets can be fun to play with, you could fund your brain wallet with 10 dollars and play the “guess it if you can” game with your friends – whoever cracks your wallet first, keeps those bucks! But jokes aside, brain wallets are probably the least secure type of self-hosted wallets out there.
Subtype: Multi-Signature Wallets
Multi-signature (multi-sig) wallet is a type of cryptocurrency wallet that requires multiple private keys to authorise a transaction. This setup distributes the control of funds among several parties, enhancing security and ensuring that no single entity can unilaterally access or transfer the funds. Multi-sig wallets are particularly useful for collaborative environments and organisations where multiple approvals are necessary for transactions.
Examples of multi-signature wallets include:
- Electrum (multi-sig): An OG Bitcoin wallet that supports multi-signature functionality. Electrum allows users to set up multi-sig wallets with customisable parameters such as plug-in hardware wallets and offline wallets, making it a flexible choice for various use cases.
- Armory: Known for being open-source and for its advanced security features, Armory offers robust multi-signature capabilities. It is designed for power users who need high security and control over their Bitcoin transactions.
Teamwork makes the dream work!
Multi-signature wallets significantly improve security by requiring multiple private keys to authorise transactions, reducing the risk of theft or unauthorised access, as an attacker would need to compromise several devices or parties to gain control over the funds.
Secondly, multi-sigs are ideal for situations where control over funds needs to be shared among multiple parties. For example, in a corporate environment, funds can be managed collectively by requiring multiple executives to approve transactions, thus ensuring accountability and reducing the likelihood of fraudulent activities.
From a cybersecurity point of view, distributing the signing authority across multiple parties eliminates single points of failure. If one private key is lost or compromised, the funds remain secure as long as the other keys are intact.
You need to transact, now! But your partner is hiking:

Since multiple signatures are needed to authorise transactions, coordinating among the key holders can be cumbersome, leading to delays in transaction approval, particularly in scenarios where the key holders are not easily accessible or available.
Setting up a multi-signature wallet can be more complex than a standard single-signature wallet. Users need to generate and manage multiple private keys, which can be technically challenging, especially for those who are not well-versed in cryptocurrency security practices.
Multisig’s Product-Market-Fit:
DAOs, on-chain funds, and treasuries often use multi-sig wallets to avoid centralisation and bring scrutiny to the process of on-chain expenditures. Looking off the chain, fund managers and custodians could also use multisite to secure their funds and avoid unauthorised distribution of their treasuries within and outside their corporations. But multisig’s have found their place beyond big businesses and on-chain organisations and entered the homes of retail users, where, as argued by Coincenter, husbands and wives set multisigs to manage their joint accounts.
Conclusion
In the realm of cryptocurrency, selecting the right wallet requires a careful balance of security, convenience, and personal needs. Each type of wallet, from hardware to paper, offers distinct advantages and trade-offs, necessitating thorough research and consideration of individual circumstances. Whether prioritising the high security of a hardware wallet, the portability of a mobile wallet, or the decentralisation of a full-node wallet, users must make informed decisions tailored to their specific use cases.
To help you with doing your own research (DYOR) on wallets, you can use WalletSecritiny for security evaluation as well as Coincarp for high-level rankings.
Remember, hackers will try to hack your wallet, deep fakes will try to make you donate, and a scammer acting like customer support might try to find out your seed – however, none of these weapons will be able to scratch you as long as you follow one simple, yet often unintentionally broken rule: Never-ever share your seed phrase with anyone, not your friends, not your boss and even not your lover. In this volatile and unforgiving world of crypto, your vigilance is your strongest safeguard.
Disclaimer: This article contains affiliate links. If you click on these links and make a purchase, we may receive a small commission at no additional cost to you. These commissions help support our work and allow us to continue providing valuable content. Thank you for your support!
This article is provided for informational purposes only and is not intended as investment advice. Investing in cryptocurrencies carries significant risks and is highly speculative. The opinions and analyses presented do not reflect the official stance of any company or entity. We strongly advise consulting with a qualified financial professional before making any investment decisions. The author and publisher assume no liability for any actions taken based on the content of this article. Always conduct your own due diligence before investing.