This deep dive serves as a detailed breakdown of Symbiotic – a permissionless staking protocol, offering a granular analysis of its 5-layer architecture.
What is Symbiotic?
Symbiotic is a decentralised shared security protocol, allowing networks and network participants to manage and align their staking and restaking strategies in a customisable and permissionless environment. To this end, Symbiotic extends beyond traditional restaking by offering a modular framework that supports multiple assets and governance models, enabling different parties to define their own rules for collateral management, operator selection, and security mechanisms.
The core idea behind Symbiotic is to create a flexible system where networks can level their decentralisation and security up, by leveraging various assets and operators without being tied to a single protocol or infrastructure. Such modularity could also support unique applications that separate governance from a financial utility or enable sovereign infrastructures secured by a protocol’s native assets, hence why the protocol was designed to cater to a wide range of use cases, from simple restaking to more complex decentralised security arrangements.
Overall, Symbiotic is a generalised shared security system enabling decentralised networks to bootstrap powerful, fully sovereign ecosystems via staking and restaking. Projects can use Symbiotic protocol to source operators and to scale economic security for their decentralised networks.
(Source: Symbiotic.fi)
Symbiotics’s architecture (as shown above) is designed to be open, permissionless, modular and flexible. Below is a review of each objective on a high level, before diving deeper into the design.
- Open: Capital deployment is highly efficient through an expandable collateral base and scalable architecture, ensuring optimal sourcing of node operators and economic security.
- Permissionless: Builders have full choice and control over shared security agreements, supported by immutable core contracts without the need for governance, slashing committees, or permissioning.
- Modular: Symbiotic acts as a minimal coordination layer that easily integrates into existing or new network architectures, providing flexibility to all market participants.
- Flexible: Networks can fully customise their reward and punishment mechanisms, with adaptable restaking logic that adjusts smoothly to evolving requirements.
By the way, for a recap on how staking and restaking work, be sure to check out our Liquid restaking guide, and do not forget to stake with us via Simply’s Multichain Staking page!
Symbiotic in Numbers:
Symbiotic was first deployed on June 11, 2024, and has raised a $5.8 million seed investment from crypto native investors like Paradigm and Cyebr.Fund.
Since the deployment, Symbiotic has demonstrated impressive growth with a Total Value Locked (TVL) surpassing $1.2 billion and currently sitting at nearly $1 billion.
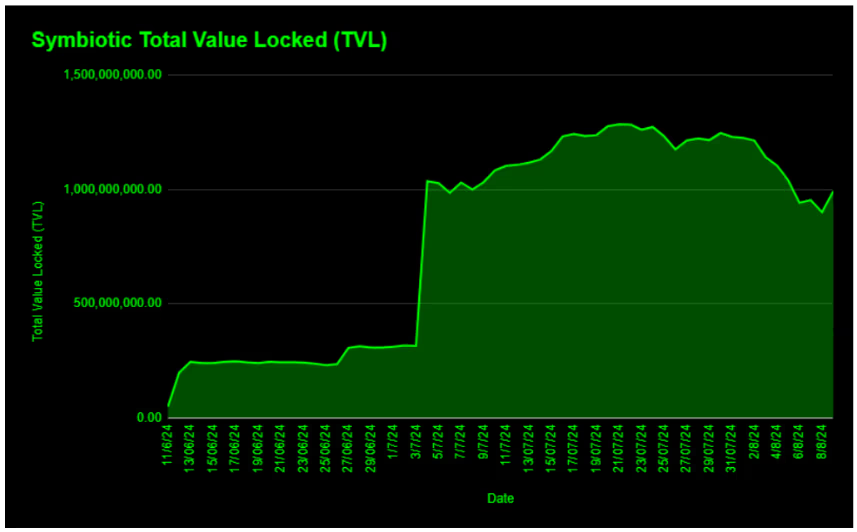
(Data: Defillama)
Moreover, just as Symbiotic supports a broader array of networks, it also enables deposits of tokens from various chains. At present, WSTETH (wrapped staked Ether) dominates the deposit pool, accounting for 64.2% of the total, with CBETH (Coinbase wrapped staked Ether) in second place, followed by WBETH (wrapped Binance Ether).
WSTETH also leads in terms of tokens by inflows over the last 6 months, followed by WEBETH and a new 3rd ranker called ENA – a native token of the Ethena network.
5 Layer Architecture
Symbiotic consists of 5 layers including economic security, staking, infrastructure, arbitration and services layers, each hosting specific stakeholders like operators and resolvers. Below we explain each layer in more detail.
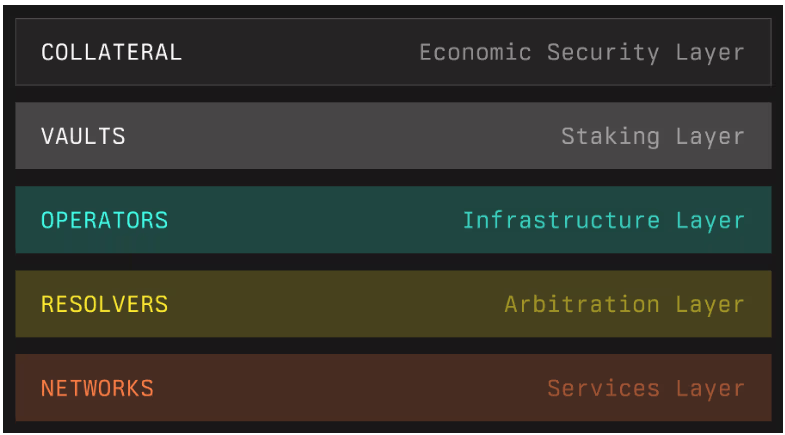
(Source: Symbiotic docs)
Collateral: Economic Security Layer
Collateral is a key concept introduced by Symbiotic to enhance capital efficiency and scalability. It allows assets used to secure Symbiotic networks to be held outside the Symbiotic protocol itself, such as in DeFi positions on networks other than Ethereum.
The migration of assets outside the protocol is possible via decoupling the ability to slash assets from the underlying asset, similar to how liquid staking tokens create tokenised representations of staked positions, like Lido’s STETH. Technically, collateral positions in Symbiotic are ERC-20 tokens with added functionality to handle slashing incidents if necessary. For instance, if a collateral token is designed to support slashing, a “Burner” mechanism should be in place to properly burn the asset.
To be more specific, if the collateral is an ETH liquid staking token (LST), it can be used as collateral if a Burner contract can withdraw ETH from the beacon chain and burn it. Similarly, if the collateral is a native asset, such as a governance token, it can also be used, with the Burner implemented as a “black-hole” contract or address.
Symbiotic enables collateral tokens to be deposited into vaults, which delegate the collateral to operators across Symbiotic networks. These vaults define the acceptable collateral and its associated Burner and networks must accept these terms, along with other conditions like slashing limits, to receive rewards. We describe Vault dynamics in more detail in the next section, but to showcase the connection between collateral and teh vault, see the diagram below, which shows how the user could mint an asset-specific collateral and deposit it into a vault, subject to potential slashing.
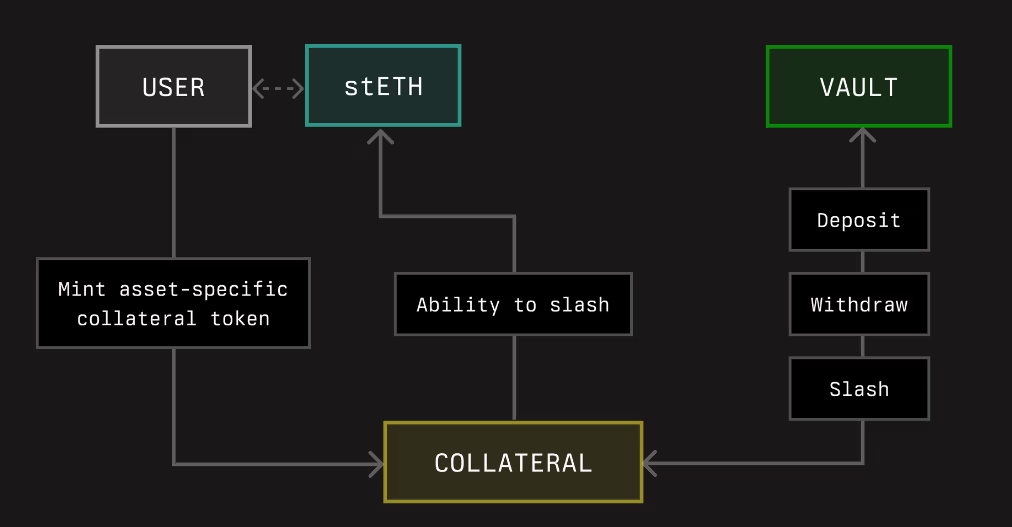
(Source: Symbiotic docs)
In summary, collateral is central to Symbiotic’s security architecture. It serves as an abstraction representing underlying on-chain assets that are chain- and asset-agnostic. Collateral within Symbiotic can include ERC-20 tokens, withdrawal credentials of Ethereum validators, or other on-chain assets such as LP positions, with no restrictions on the blockchains these positions are held on.
Vaults: Staking Layer
Vaults form the delegation and restaking management layer within Symbiotic, handling three pivotal aspects of its ecosystem:
- Accounting: Vaults oversee the processes of depositing, withdrawing, and slashing collaterals, along with managing their underlying assets.
- Delegation Strategies: They allow vault deployers or owners to define how assets are delegated and restaked to operators across various Symbiotic networks. Importantly, these networks must opt into the proposed strategies.
- Reward Distribution: Vaults are responsible for distributing staking rewards from networks back to the individuals or entities that deposited the collateral.
The diagram below illustrates how vaults support the above-mentioned functionalities. For example, before the user’s delegation strategy reaches operators or restaking terms are communicated to networks, the user must deposit via a vault.
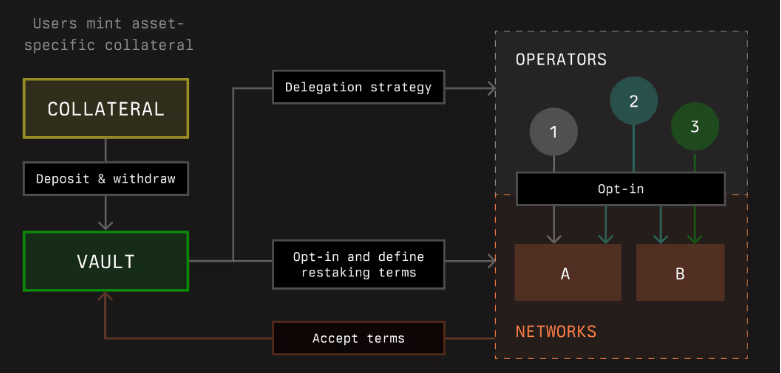
(Source: Symbiotic docs)
Symbiotic-designed vaults are highly adaptable, meaning that they can be set up in an immutable, pre-configured manner, ensuring that their parameters remain unchanged. Alternatively, vaults can be configured by an owner who retains the ability to update vault settings. Such configuration flexibility enables operators and curators—such as crypto institutions or liquid (re)staking protocols—to craft specialised products. Examples include:
- Operator-Specific Vaults: Operators can create vaults that restake collateral within their own infrastructure across any selection of networks. Hence, allowing an operator to maintain multiple vaults with varied configurations, catering to different client needs without the necessity for additional node infrastructure.
- Curated Multi-Operator Vaults offer curated configurations that involve restaking across multiple networks and delegation strategies to a diversified set of operators. They can also set custom slashing limits, capping the amount of collateral that can be slashed for specific operators or networks. However, for the set configurations to be effective, the networks in question must accept the terms set by the vaults.
- Immutable Pre-Configured Vault are deployed with fixed rules that cannot be altered, therefore providing increased security for users who might be wary of the risks associated with a vault curator. Such risk could include the curator’s ability to add new restaked networks or modify existing configurations.
In essence, vaults are integral to Symbiotic’s security and operational framework, providing a flexible platform for managing assets, delegating them to operators, and distributing rewards across the network.
Operators: Infrastructure Layer
Operators are entities responsible for running the infrastructure for decentralised networks, both within and outside the Symbiotic ecosystem. The Symbiotic protocol maintains a registry of these operators, recording interactions with the protocol and allowing participants to attach credentials and other relevant data to operator entities. In its initial version, the registry includes operator metadata provided by the operators themselves, as well as data generated through interactions with the Symbiotic protocol, such as:
- Networks the operator has opted into
- Associated vaults and restaked collateral from those vaults
- Historical logs of slashing incidents and all other interactions within the Symbiotic ecosystem
A significant advantage of the Symbiotic protocol, along with its integrated vault system, is the ability for operators to receive stakes from various partners (through vaults) to support the same set of node infrastructure across different networks. Such open system enables node operators to secure stakes from a diverse group of stakers with varying risk profiles without needing to set up separate infrastructure for each.
When it comes to operator onboarding, when an operator opts into a network, they signal their intent to validate it. Each network then independently decides whether to include the operator in its active operator set, based on factors like reputation, stake amount, and other relevant criteria. Once the operator’s stake is active, it is immediately subject to slashing after the opt-in process for both the network and the vault. However, the vault may apply a timelock for allocating the stake, providing additional guarantees for operators.
The open process is shown in the diagram below, where for example, we can point out that an operator-specific primitive is connected to Networks 1, 2 and 3.
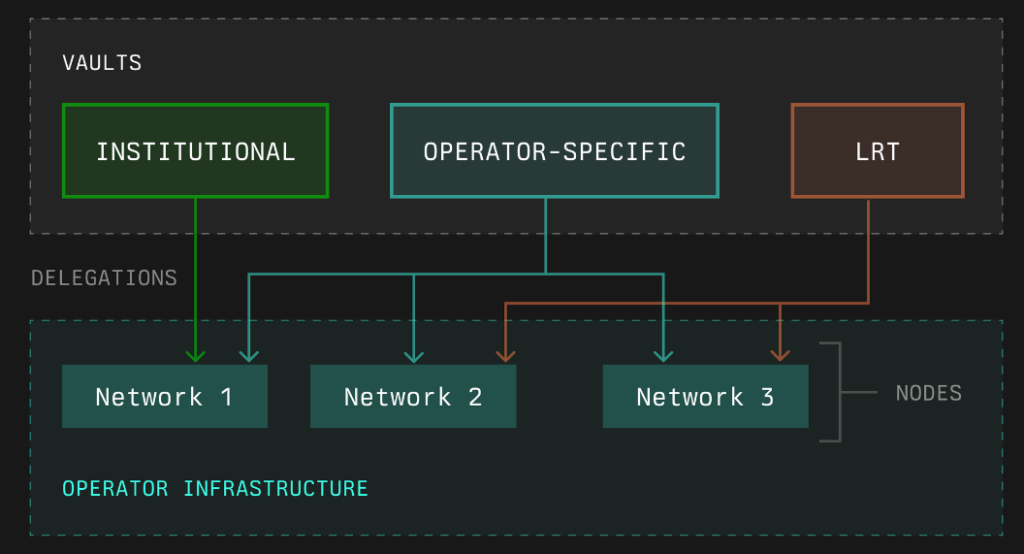
(Source: Symbiotic docs)
Looking ahead, the Symbiotic protocol aims to develop a comprehensive set of verifiable data and curated credentials for node operators, allowing future networks using Symbiotic to source security for their use cases through innovative, reputation-based operator selection mechanisms that maximise capital efficiency.
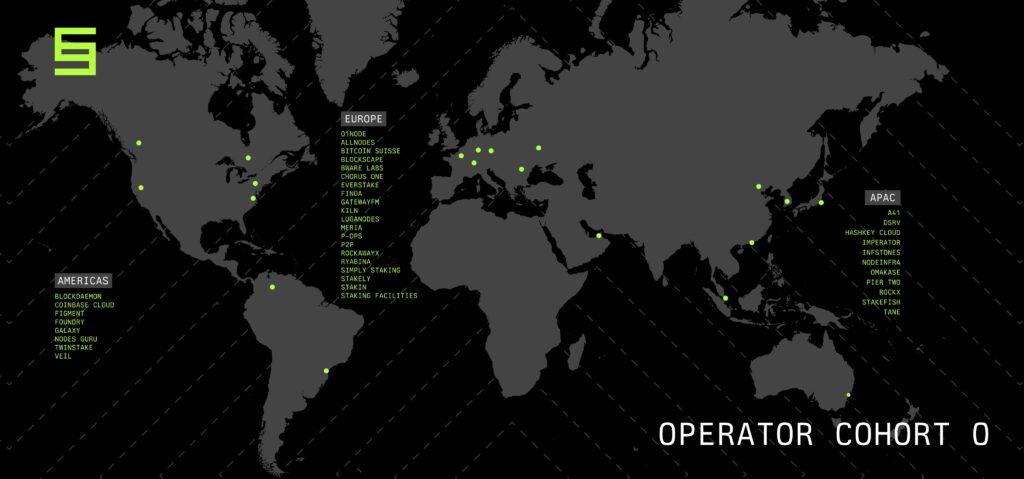
Last but not least, as shown on this map, Symbiotic fosters a global cohort of top-performing operators such as Bitcoin Suisse and Coinbase Cloud, and Simply Staking is proud to be one of the early supporters of the protocol!
Resolvers: Arbitration Layer
Resolvers are entities or contracts responsible for approving or vetoing slashing penalties imposed on operators in networks where they provide services. These resolvers are mutually agreed upon by vaults, which represent the providers of economic security, and the networks they secure.
Further, Resolvers can be fully automated, especially for slashing penalties that are objectively verifiable (hence removing human error and bias), or they can take the form of entities such as slashing committees or external dispute resolution frameworks. By acting as a neutral third party to arbitrate penalties, resolvers enable networks and restakers to share collateral with confidence.
Symbiotic introduced resolvers to support various methods of managing slashing incidents where the choice of resolvers is guided by the terms proposed by networks and accepted by vaults that aim to back operators with collateral. For example, as shown below, a vault can designate different resolvers for different portions of its collateral – 10% might be left without a resolver, 40% could be managed by Resolver A, and the remaining 50% by Resolver B, both of which might be committees responsible for specific network subsets.
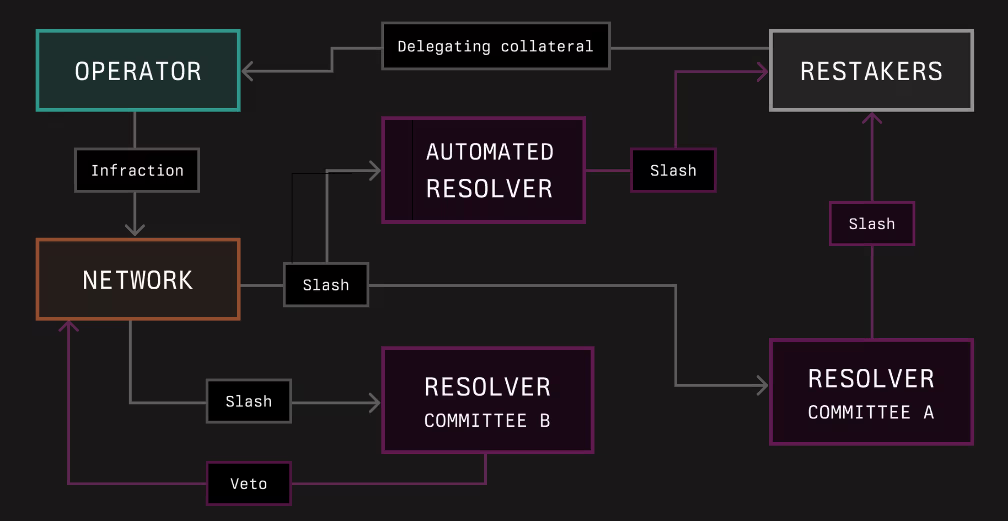
(Source: Symbiotic docs)
Additionally, third-party decentralised dispute resolution frameworks that are outside Symbiotic protocol, such as UMA or Kleros, can serve as resolvers. In some cases, a quorum of resolvers may be required to either veto or approve a particular slashing incident, providing added security assurances for participants in the Symbiotic protocol.
Overall, resolvers act as pre-configured enforcement bodies that trigger actions automatically, based on set conditions and rules, hence acting as key pieces of governance and rule deployment.
Networks: Services Layer
Symbiotic defines a network as any protocol requiring decentralised infrastructure to deliver services within the crypto economy. Examples include enabling developers to launch decentralised applications by handling transaction validation and ordering, providing off-chain data to crypto applications, or offering guarantees for cross-network interactions.
Decentralised infrastructure networks can leverage Symbiotic to source security through operators and economic backing. Protocols may consist of multiple sub-networks with distinct infrastructure roles, where developers can specify rules that participants must follow to engage with any of these sub-networks.
Networks are represented by a network address (either an externally owned account (EOA) or a smart contract) and a middleware contract that includes custom logic, particularly slashing logic. The core functionalities of the protocol include slashing operators and rewarding both stakers and operators
Furthermore, each network includes an epoch – a period during which a specific set of operators, determined by the captured stake, serves the network. The combined duration of the network epoch and the vault’s veto and execution phases must not exceed the vault’s epoch duration to ensure withdrawals do not affect the captured stake.
The network also hosts the nodes/delegators, to whom the vaults distribute the staking rewards. The vault manages stakes by setting limits for networks and operators and it’s delegator module allocates stakes, while the slasher module manages slashing incidents. The current active balance of the vault, along with established limits, determines the stake for the next network epoch.
In the backend, the end-to-end staking process includes several steps:
- The network registers itself by calling the network registry.
- The network opts into the vault through a dedicated service.
- Operators opt into both the vault and the network.
- Stakers deposit funds into the vault.
- The network sets a maximum stake amount for the vault.
- Specific roles define stake limits for the network and operator-network pairs.
- The staked amount cannot be withdrawn for at least one epoch, except in cases of cross-slashing.
Networks can slash operators within the vault if certain conditions are met:
- The network is opted into the vault.
- The operator is opted into both the vault and the network.
To start slashing, networks use a module that checks guarantees and calculates how much slashing has happened so far. Slashing can only happen if it stays within the allowed limit based on those guarantees.
Overall, networks act as clients of Symbiotic’s architecture, utilising its security-sharing model, while bringing liquidity and delegators to the protocol.
Conclusion
Symbiotic’s architecture provides a structured framework that addresses the needs of decentralised networks seeking customisable and scalable security solutions. Through its modular design, Symbiotic allows networks to manage staking and restaking strategies with a high degree of flexibility, enabling the integration of various assets and governance models. The system’s layered approach, encompassing economic security, staking, infrastructure, arbitration, and services, offers a solid foundation that accommodates diverse use cases, from basic restaking to complex decentralised security arrangements.
The protocol’s use of collateral, vaults, operators, resolvers, and network services facilitates a permissionless environment where participants can interact securely and efficiently. By enabling networks to tailor their security mechanisms, Symbiotic not only enhances decentralisation but also supports the creation of sovereign ecosystems. The integration of automated arbitration processes, customisable operator configurations, and adaptable staking mechanisms highlights Symbiotic’s interesting approach to (re)staking.
You can simply stake and secure your assets with the Ledger wallet.
Disclaimer: This article contains affiliate links. If you click on these links and make a purchase, we may receive a small commission at no additional cost to you. These commissions help support our work and allow us to continue providing valuable content. Thank you for your support!
This article is provided for informational purposes only and is not intended as investment advice. Investing in cryptocurrencies carries significant risks and is highly speculative. The opinions and analyses presented do not reflect the official stance of any company or entity. We strongly advise consulting with a qualified financial professional before making any investment decisions. The author and publisher assume no liability for any actions taken based on the content of this article. Always conduct your own due diligence before investing.