Introduction
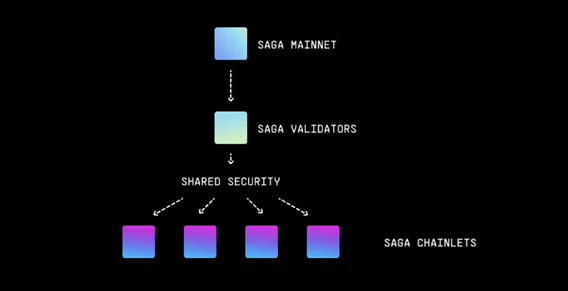
Saga is the Layer-1 to launch Layer-1s. A network designed to launch other app-specific blockchains, or as they call them ‘Chainlets’.
You might be interested in these articles:
Infinite horizontal scalability is the fundamental ethos of Saga.
A Chainlet encompasses all of the necessary components needed to launch a dedicated blockchain thanks to the integrated stack offered by Saga.
Historically, launching your own blockchain was a complex task of balancing the blockchain trilemma, the emergence of a more modular stack fixed some of those issues but left developers with a harder task at times balancing all of the different aspects of a blockchain such as piecing together the appropriate Data Availability, Consensus, and Settlement layers.
By focusing on scalability, security, and ease of use, Saga tackles common challenges such as high costs and complicated setups, significantly reducing entry barriers for developers. This is achieved through a unique model of shared security, where Saga leverages a collective validator setup. This shared model ensures that each independently operated blockchain maintains stability, seamless upgrades, and effective congestion management without the need for developers to manage their own security infrastructure.
Why Saga?

The technical architecture of Saga allows it to handle high-throughput making the network able to target the Web3 gaming and entertainment sector. These sectors are demanding on infrastructure and often time require strict SLAs (such as near perfect uptime).
Saga’s advancements in blockchain technology facilitate the processing of high-volume-low-value types of transactions – the types that the gaming and multiverse industry require. However, while it is fast-growing, they are still nascent. That’s why Saga is positioning itself in line with the principles of Web3, particularly DeFi. That is why SAGA is aligning itself with the principles of Web3, particularly DeFi.
Chainlets Explained
Saga is a protocol that simplifies the process of creating application-specific blockchains, termed “Chainlets”. Each Chainlet is securely linked to the Saga Mainnet through Cosmos Interchain Security, utilising a system called Optimistic Coordination.
This system employs the same set of validators across all Chainlets, who must adhere to strict service-level agreements (SLAs) and are held accountable for any security breaches, ensuring a robust and reliable safeguarding framework. Should a break of the SLAs occur, that validators infraction would be reported via Inter Blockchain Communication (IBC) by the rest of the validators to the mainnet. This would trigger a slashing event to occur on that validator to ensure that they acknowledge the actions of their discretion.
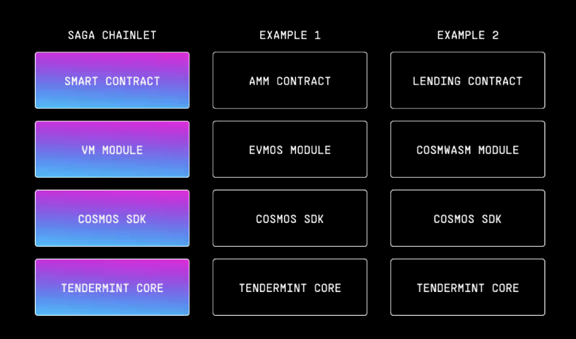
This uniform security protocol allows developers to deploy smart contracts on independent blockchains, each equipped with their chosen virtual machine, enhancing both security and operational efficiency.
Each Chainlet, running on its dedicated virtual machine, offers key advantages to developers:
- Simplified deployment: Launching a Chainlet is as easy as deploying a smart contract, but without the complications of shared block space. This process is enhanced by an automated CI/CD pipeline that standardised deployments across single-tenant VMs, significantly boosting Saga’s operational efficiency and reducing time-to-market for developers applications. Deploying a Chainlet on Saga is a 1-minute process on its WebApp and can be done by non-developers.
- VM Agnosticism and customisation: Saga’s infrastructure supports a variety of virtual machines, including EVM, CosmWasm, and others, allowing developers the flexibility to select and customise the VM that best fits their application’s needs. This VM agnosticism extends to enabling developers to tailor other blockchain components, offering unprecedented flexibility and control over the blockchain environment.
- Independent upgradability: Components such as VM modules, SDKs, and Tendermint Core can be upgraded without affecting other applications or the mainnet, minimising downtime and interference.
- Enhanced scalability through horizontal scaling: Saga enables developers to effectively manage higher demand by manually sharding different workflows into multiple Chainlets. This horizontal scaling is crucial for applications that require high throughput and scalability, such as decentralised finance platforms, where performance can directly influence user experience and platform reliability.
Shared Security of Chainlets – Inspiration from Cosmos
Saga and Cosmos share similarities in how security is shared across the chainlets and consumer chains respectively. The codebase of Interchain Securit (ICS) and Cross Chain Validation (CCV) are very similar, especially considering Saga uses the same codebase (at least a version of it now since ICS is moving towards Partial Set Security (PSS)).
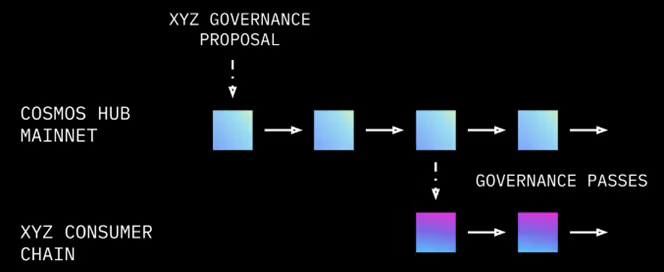
There are a few key distinctions that need to be made between the two systems, however.
The current iteration of Interchain Security which is Replicated Security, and even the 1st phase of the new Partial Set Security is governance-gated. This means that all projects wishing to tap into the underlying economic security and become part of the ‘ATOM Economic Zone’ (AEZ) must go through the tedious process of convincing governance to approve their status as a consumer chain.
Saga, on the other hand, allows for a developer or chainlet, to permissionlessly tap into the security of Saga. This is down to the fact that developers on Saga are only allowed to utilise VMs that have been audited by Saga which reduces the risks of exploits.
Tokenomic Design and Flow
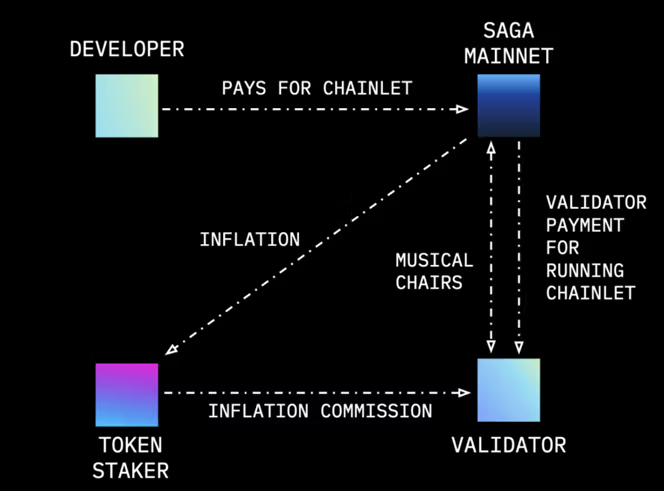
The Saga token design involves various parties interacting with one part of the network to ensure the continuous function and deployment of permissionless chainlets. Saga’s approach to tokenomics emphasises permissionless infrastructure deployment, prioritisation of usability for developers, and cost-effective pricing.
For simplification, we will split the mechanism into two distinct categories, the Front-End and the Back-End.
Front-End: End User to the Developer
End User Flow: Separation of Infrastructure and Application
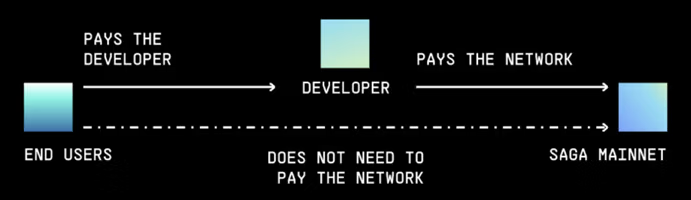
The topology of Saga changes the way that end-users have to pay for using the network. In traditional blockchain systems, the end-user would have to pay the network. Due to the way that Saga is designed, the end-user does not have to pay for the network but instead would pay the developer for the product (chainlet) that they make use of. The developer is the one tasked with paying the network (chainlet fee deposit).
Saga is the first network that decouples the infrastructure from the application which gives more flexibility to the end-user as well as the developer.
Back-End: Developer to the Mainnet
Foundations: Chainlet Deposit Fee
The blockspace for Chainlets is provisioned using a credit system. A developer wishing to launch a Chainlet has to first ‘pre-pay’ through a deposit with $SAGA (or other tokens). The account that is funded acts as a pre-paid account where the amount is consistently drawn down based on chainlet usage. Once the account is empty, the chainlet will shut down until the developer can fund the deposit once again.
Developers Flow: Paying for the Chainlet (Credit system)
A developer at the beginning of every epoch (1 day typically) would have to pay the chainlet fee (the cost to run the chainlet which was determined in the Musical Chair process by Validators). The cost to the developer, however, is not just the price set by the validators but is the cost multiplied by the number of validators in the Active Set (currently at 21). This is so every validator receives the price they set in the musical chair process and not a fraction of it.
How do Validators Price the Chainlet?
This is done through a feature they call ‘Musical Chairs’ – an innovative way for validators to price chainlets.
A Validator would publicly post the price they wish to charge a chainlet to run for 1 epoch (typically a day). These prices would be locked in shortly before the epoch is set to start and the process of Musical Chairs would begin.
The process is made up of various parts. The players are the validators chosen (set by a parameter p) from the Active set. These players would be roped into the Musical Chair auction with their locked-in prices. The validators with the cheapest bids would be included in the ‘winning set’ (the winning set has a capacity denoted by w). The rest of the validators outside of the winning set would be put into the ‘losing set’.
From the winning set, the price set for the Chainlet would be the most expensive bid from a validator.
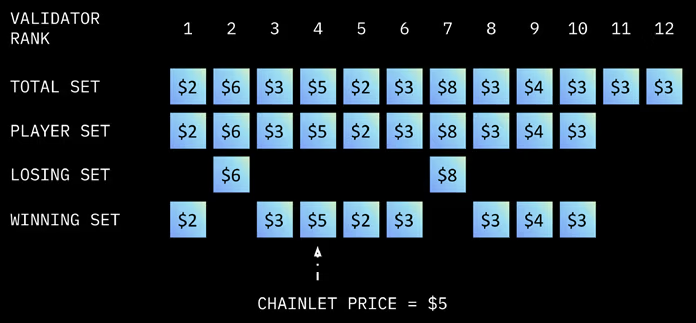
The Rewards and Punishment for those in the Winning set and the Losing set are still underworks however it is important to note that the system Saga is working towards is quite a fair system for both the developer who has to pay the validators (the network) and the validators who aren’t allowed to overcharge the developer of the chainlet (unless there is large scale collusion).
What’s next for Saga?
Saga launched phase one of their mainnet in April 2024. The hype behind the much-anticipated launch was confirmed after Binance stated that over $13B of BNB and FDUSD was staked on their launchpool in an attempt for the users of the exchange to get some of the 45M $SAGA tokens that were allocated for users on that platform.
You can Simply Stake and Secure your assets with the Ledger wallet.
Phases of Launch
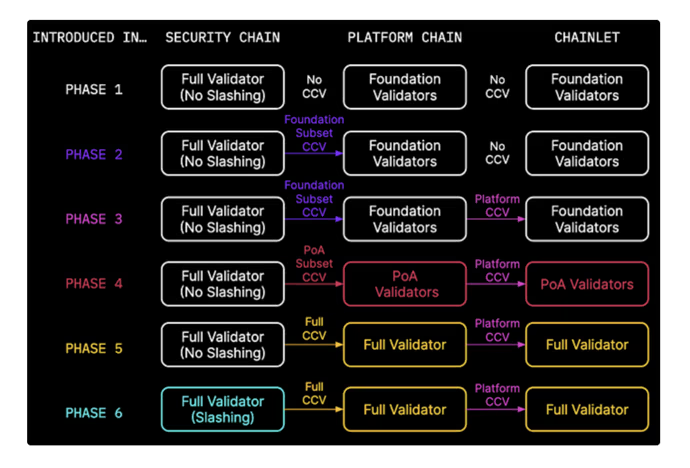
Saga’s mainnet development is strategically structured into 6 distinct launch phases. The structured and phased approach ensures throughout testing and validation of each phase before moving on to the next phase.
Phase One
- The initial phase focuses on establishing a robust security and platform architecture. This phase sees the launch of the security chain as well as the first iteration of the platform chain. In this initial phase, chainlet deployment on the platform chain will be gated (permissioned) with the deployment progressively transitioning toward a permissionless nature as the other phases of mainnet launch go live.
Phases Two – Six: Expansion and enhancement
Following the foundational stage, phases two through six are dedicated to introducing a breadth of new functionalities. These phases are meticulously planned to progressively expand the network’s capabilities, enhancing features such as cross-chain interoperability, advanced governance models, and more sophisticated economic structures.
Throughout the phases, Saga will gradually transition Cross Chain Validation onto the mainnet. Below is a high-level overview of how they plan to do this on a phase-by-phase basis:
- Phase Two: The connection between the security chain and platform chain involves using foundation subset shared security.
- Phase Three: This phase involves the chainlet receiving shared security from the platform chain through the use of foundation validators.
- Phase Four: The transition of security to the validator set begins. Saga will sunset their validators providing security and opt for a PoA approach initially.
- Phase Five: The platform chain is now run by all 21 validators, and all chainlets are also run by these validators.
- Phase Six: Once all the active set validators are running CCV for the security and platform chains, slashing can begin. Slashing is there to penalise misbehaving validators.
Conclusion
Saga is changing the blockchain landscape by enabling the seamless launch of app-specific blockchains, or “Chainlets,” through its own Layer-1 protocol. Their approach addresses critical challenges in blockchain development such as scalability, security, and ease of deployment. By offering a simplified, horizontally scalable, and secure infrastructure, Saga significantly lowers the barriers for developers, making it an attractive platform for Web3 gaming, entertainment, and DeFi sectors.
Saga’s technical architecture, featuring shared security and VM agnosticism, allows developers to deploy customized Chainlets with minimal effort. This unique model, inspired by the Cosmos ecosystem, ensures robust security and operational efficiency while enabling independent upgrades and enhanced scalability.
In conclusion, Saga has the potential for great blockchain innovation. Its ability to provide scalable, secure, and easy-to-deploy Chainlets offers a compelling value proposition for developers.
Disclaimer: This article contains affiliate links. If you click on these links and make a purchase, we may receive a small commission at no additional cost to you. These commissions help support our work and allow us to continue providing valuable content. Thank you for your support!
This article is provided for informational purposes only and is not intended as investment advice. Investing in cryptocurrencies carries significant risks and is highly speculative. The opinions and analyses presented do not reflect the official stance of any company or entity. We strongly advise consulting with a qualified financial professional before making any investment decisions. The author and publisher assume no liability for any actions taken based on the content of this article. Always conduct your own due diligence before investing.